
Contact Us
Phone: +974 7470 3333 Email: info@shieldtechnology.com

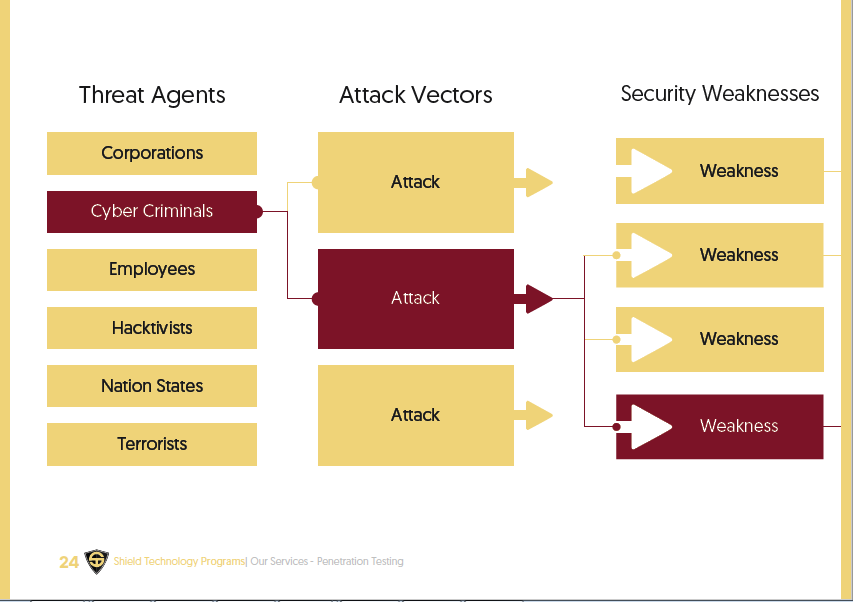
Penetration Testing is the art of legal or ethical hacking where a security specialist or team of specialist tests and documents the security or protection of a system by
breaking into it with the exception of very disruptive attacks that may affect critical business operations.
Web Pen-Testing
Application Pen-Testing
Network Pen-Testing
1. Foot Printing
Determining the targets footprint, e.g. DNS records, IP scope, public information, contract information, etc.
2. Scanning
Determining the target openings, e.g. service ports, wireless networks, modem pools, vpn servers, etc.
3. Enumeration
Determining the services behind the opening, e.g. webservers, systems, routers, firewalls, Wi-Fi authentication, etc.
4. Penetration
Selecting appropriate exploits and penetrate the target, e.g. SQL injection, buffer overflow, password attacks, etc.
5. Escalation
Escalation of the credentials to admin or root, e.g. dll injection, local exploit, configuration change, schedule jobs, etc.
6. Getting Interactive
Getting a remote shell or GUI on the target, e.g. RDP, VNC, NetCat, etc.
7. Expanding Influence
Moving from the initial target as a foothold or beach-head to the rest of the network taking over the domain.
8. Cleaning Up
Ensuring backdoors and removing evidence, e.g. rootkits, log removal, log editing, etc.
9. Reporting
Writing and presenting a report on the pen-test to the owners of the network one had authorization to test.
Penetration testing is the only way to fully ensure that your site is imprenetrable from external attacs and that you are able to demonstrate cybery security.
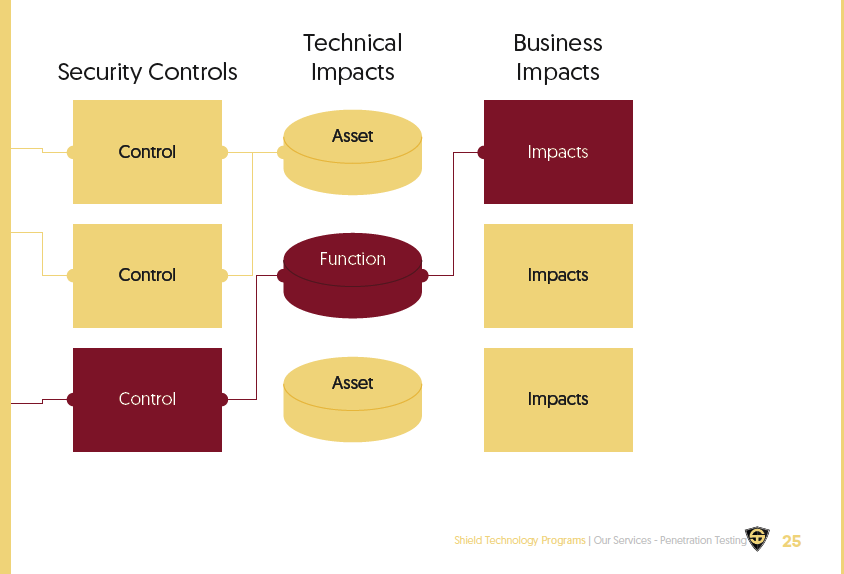
The purpose of the analysis is to simulate an attack to assess your immunity level, discover vulnerabilities and provie recommendations and guidelines to make your IT infrastructure secure.
Each test results produces two high level reports: a technical report for IT personnel and a management report aimed at directors and investors which details the high risk, medium risk and low risk vulnerabilities detected.
The reports discuss in detail the relevant issues and routes that can be used by attackers to compromise and gain unauthorized access to sensitive information. Each issue highlighted inclues an overview, analysis and security guidelines, which - if followed correctly will enable the confidentiality and integrity of your systems and applications.
These penetration tests look for security vulnerabilities in a web-based application or program deployed and installed on a target environment.
This is one of the most common types of penetration tests, and involves finding target systems on the network, searching for openings in their base operating systems and available network services, and then exploiting them remotely.